OIDC State cookie not found #1050
Replies: 4 comments 17 replies
-
|
Firstly, you should not run over plain HTTP... |
Beta Was this translation helpful? Give feedback.
-
|
it looks like a mismatch in hostname used for accessing the application and the redirect URI; there should also be a warning about that in the logs; what is the URL that you're using in the browser to access the protected application? |
Beta Was this translation helpful? Give feedback.
-
|
upon hitting the protected website there's a redirect with an authentication request returned, including a |
Beta Was this translation helpful? Give feedback.
-
|
Hey James, I am also facing same issue.Can you tell whether you have got solution or not? |
Beta Was this translation helpful? Give feedback.
Uh oh!
There was an error while loading. Please reload this page.
Uh oh!
There was an error while loading. Please reload this page.
-
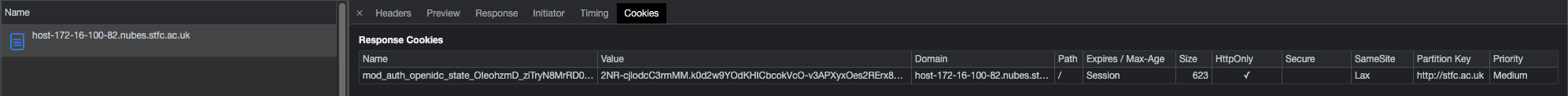
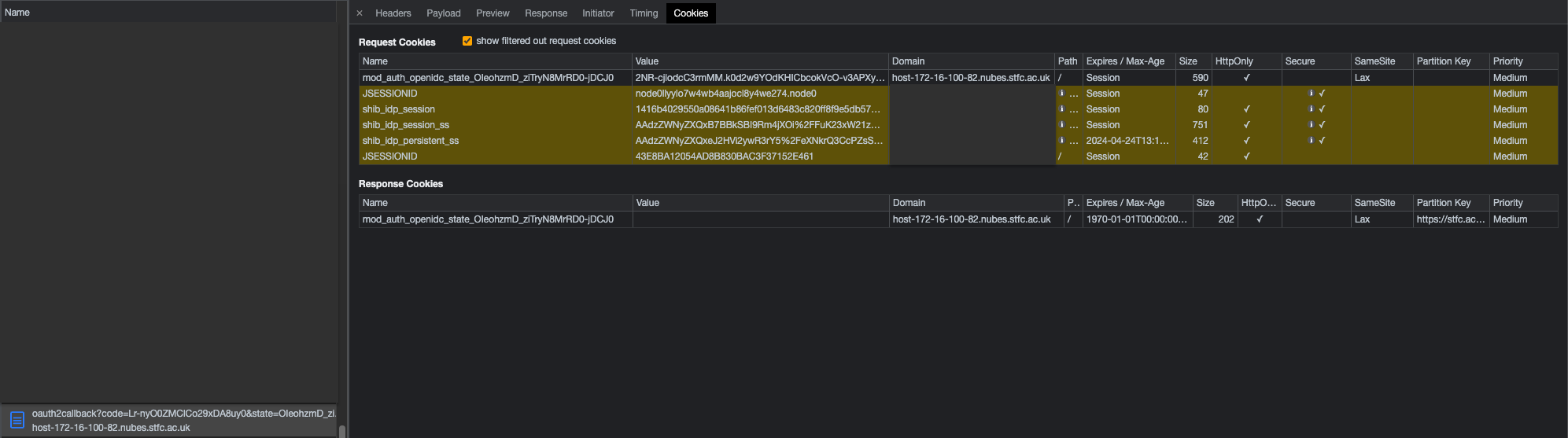
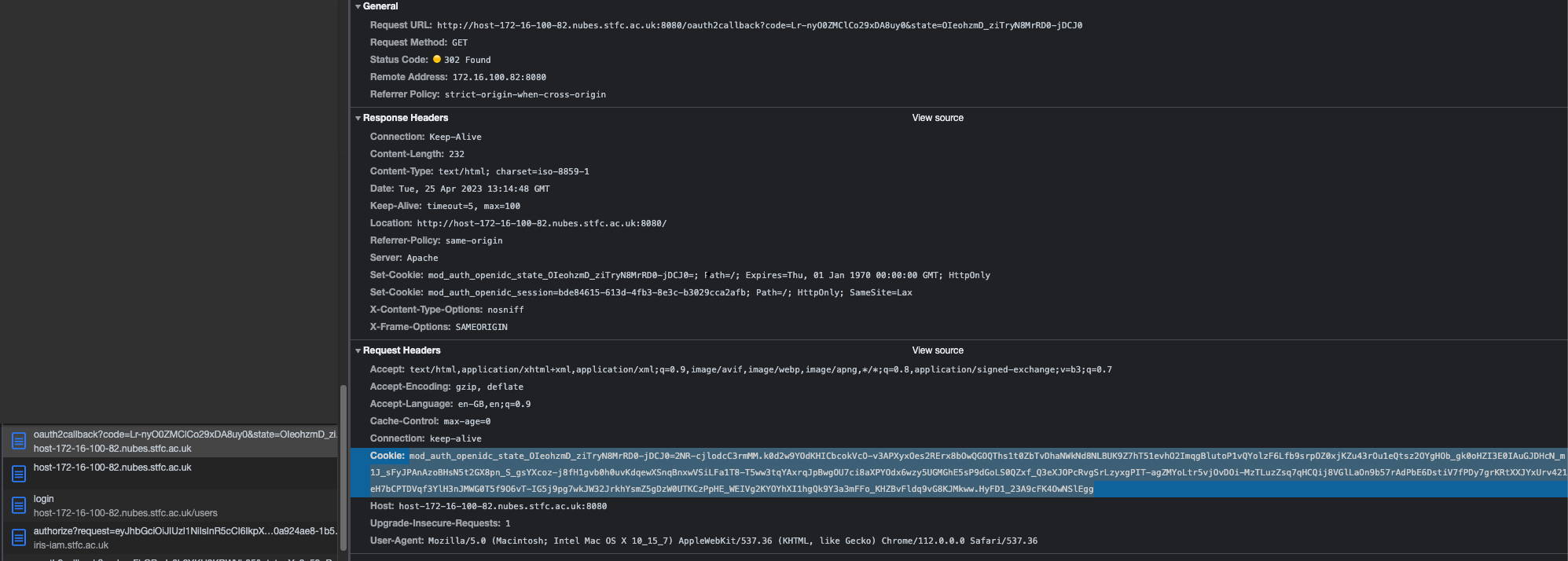
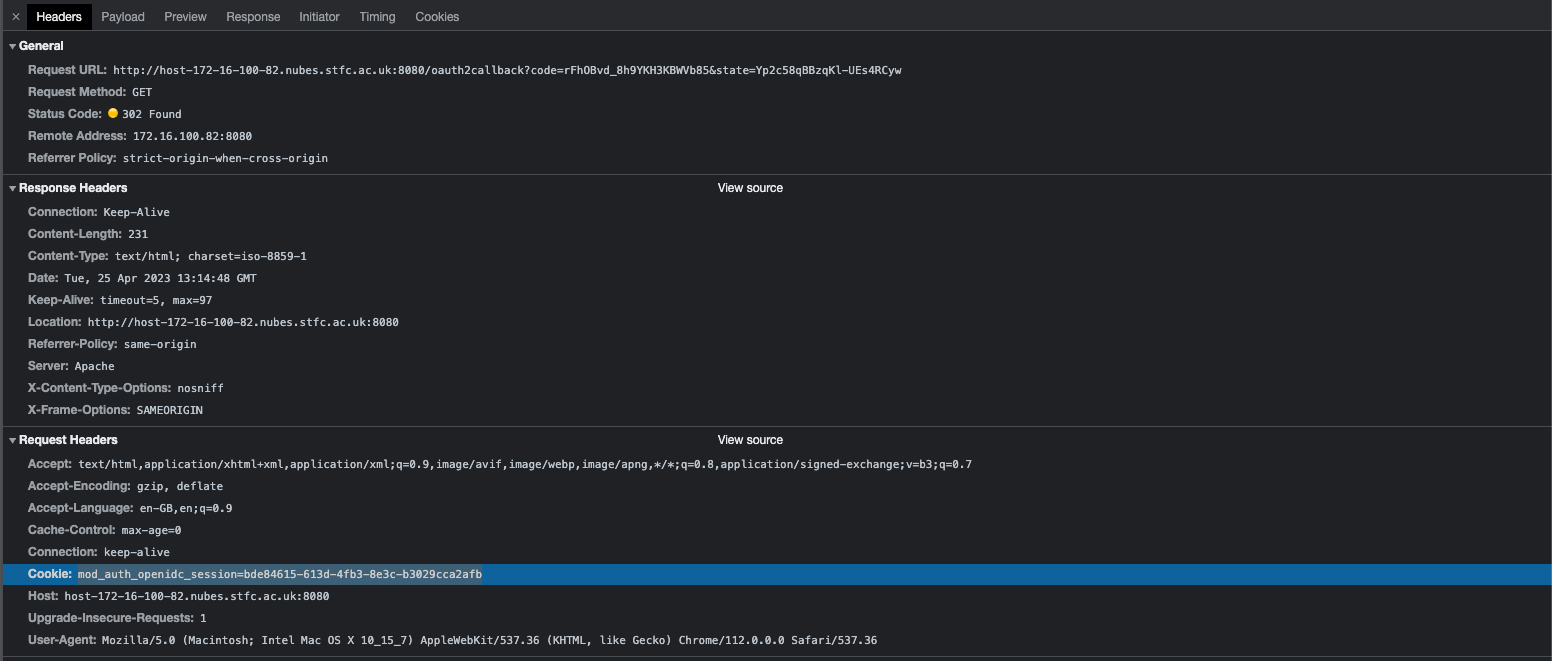
Hi. I'm attempting to use mod_auth_openidc but I'm seeing 'no state cookie found' errors. After login, the state cookie goes missing, and mod_auth_openidc redirects me back to the homepage, which redirects me back to the OIDC provider and a loop ensues, broken by a 'too many redirects' error in the browser.
Snapshot of apache debug logs, just before the error (client IP & hostname redacted):
Relevant config file (hostname replaced with {server_hostname}, OIDC provider replaced with {provider}):
ServerTokens Prod ServerName {server_hostname}:8080 # Include request ID header in accesss log LogFormat "%h %{X-Request-Id}i %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-Agent}i\"" combined LogLevel debug <VirtualHost *:80> DocumentRoot /var/www/MISP/app/webroot ErrorDocument 401 /401.html ErrorDocument 403 /401.html ErrorDocument 500 /500.html ErrorDocument 503 /503.html ErrorDocument 504 /504.html Alias /401.html /var/www/html/401.shtml Alias /500.html /var/www/html/500.shtml Alias /503.html /var/www/html/503.shtml Alias /504.html /var/www/html/504.shtml <Directory /var/www/html/> Options +Includes </Directory> # Allow access to error page without authentication <LocationMatch "/(401|500).html"> Satisfy any </LocationMatch> # Allow to access fpm-status just from localhost <LocationMatch "/fpm-status"> Require local ProxyPass "unix:/run/php-fpm/www.sock|fcgi://127.0.0.1:9000" </LocationMatch> SetEnvIf Authorization "(.*)" HTTP_AUTHORIZATION=$1 DirectoryIndex /index.php index.php <FilesMatch \.php$> SetHandler "proxy:unix:/run/php-fpm/www.sock|fcgi://127.0.0.1:9000" </FilesMatch> RewriteEngine On # Check if authkey is valid before we let apache to touch PHP RewriteMap authkeys "prg:/var/www/MISP/app/Console/cake user authkey_valid" apache:apache <Directory /var/www/MISP/app/webroot> Options -Indexes Require all granted # If request contains Authorization header and it is not request for fpm-status, check if authorizatzion key is valid. # This adds another level of protection. RewriteCond %{HTTP:Authorization} "^[a-zA-Z0-9]{40}$" RewriteCond %{REQUEST_URI} !^/fpm-status RewriteCond ${authkeys:%{HTTP:Authorization}|0} "!=1" # If authkey is not valid, return forbidden error RewriteRule .* - [F,L] # Standard MISP rules that will allow processing requests by PHP if it is not directory or file RewriteCond %{REQUEST_FILENAME} !-d RewriteCond %{REQUEST_FILENAME} !-f RewriteRule ^(.*)$ index.php?/$1 [QSA,L] </Directory> OIDCProviderMetadataURL https://{provider}/.well-known/openid-configuration OIDCRedirectURI http://{server_hostname}:8080/oauth2callback OIDCCryptoPassphrase {secret} OIDCClientID {secret} OIDCClientSecret {secret} OIDCDefaultURL http://{server_hostname}:8080 OIDCCookieSameSite On OIDCProviderTokenEndpointAuth client_secret_jwt OIDCPKCEMethod S256 OIDCScope "openid email profile" OIDCHTMLErrorTemplate /var/www/html/oidc.html # Allow access if header contains Authorization header and value in MISP format <If "-T req('Authorization') && req('Authorization') =~ /^[a-zA-Z0-9]{40}$/"> Require all granted AuthType None </If> <Else> AuthType openid-connect Require claim "groups~misp*" </Else> TimeOut 310 ServerSignature Off # Set request ID if not set from reverse proxy RequestHeader setifempty X-Request-Id %{UNIQUE_ID}e Header always set X-Content-Type-Options nosniff Header always set X-Frame-Options SAMEORIGIN Header always set Referrer-Policy same-origin <Location "/webfonts/"> # Cache for one year Header always set Cache-Control "max-age=31536000; immutable" </Location> # Enable brotli ouput compression AddOutputFilterByType BROTLI_COMPRESS text/html text/plain text/xml text/css text/javascript application/x-javascript application/javascript application/json application/x-font-ttf image/svg+xml </VirtualHost>Some things that seem weird to me:
From the wiki on state cookies:
Two possibilities in my mind:
I'm struggling to identify the cause of the error, any help would be greatly appreciated 🙂
Beta Was this translation helpful? Give feedback.
All reactions